25+ tcp state transition diagram in computer networks
INTRODUCTION The Transmission Control Protocol TCP is intended for use as a highly reliable host-to-host protocol between hosts in packet-switched computer communication networks. Rubin described the Android project as having tremendous potential in developing smarter mobile devices that are more aware of its owners location and preferences.
2
RFC 2131 Dynamic Host Configuration Protocol March 1997 12 Related Work There are several Internet protocols and related mechanisms that address some parts of the dynamic host configuration problem.

. Remote access A host-to-network configuration is analogous to connecting a computer to a local area network. - The TLS 12 version negotiation mechanism has been deprecated in favor of a. For example B may be receiving requests from many clients other than A andor forwarding.
Location of an end point signal of a desire to communicate negotiation of session parameters to establish the session and teardown of the session once established. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. 129 124 112 81 55 44 40 27 21 5 TRANSMISSION CONTROL PROTOCOL DARPA INTERNET PROGRAM PROTOCOL SPECIFICATION 1.
Session Initiation Protocol June 2002 The first example shows the basic functions of SIP. Figure 1 shows a typical example of a SIP message exchange between two users Alice and Bob. Was founded in Palo Alto California in October 2003 by Andy Rubin Rich Miner Nick Sears and Chris White.
Packets are normally quite smaller as the network hardware can be a limiting factor. BitTorrent clients are available for. The typical network symbol for a server is a box that resembles a computer tower.
GPS coordinates of the accommodation Latitude 43825N BANDOL T2 of 36 m2 for 3 people max in a villa with garden and swimming pool to be shared with the owners 5 mins from the coastal path. Virtual private networks may be classified into several categories. The early intentions of the company were to develop an advanced operating system for digital.
This data may be incomplete but improves the performance of the retrieval process when non-local data is repeatedly accessed. On a network diagram the typical symbol for a VPN is a padlock. The Open Systems Interconnection model OSI model is a conceptual model that provides a common basis for the coordination of ISO standards development for the purpose of systems interconnection.
The Reverse Address Resolution Protocol RARP through the extensions defined in the Dynamic RARP DRARP explicitly addresses the problem of. RFC 2616 HTTP11 June 1999 may apply only to the connection with the nearest non-tunnel neighbor only to the end-points of the chain or to all connections along the chain. This type provides access to an enterprise network such as an intranetThis may be employed for remote workers who need access to private resources or to enable a mobile worker to access.
ピアスに関するqa 販売しているピアスはすべて2個売りですか ピアスは2個売りとなっております 一部の特殊な形状のピアスや片耳用のピアスは1個売りとなっております. The second kind of data is cached data which was acquired by a local resolver. RFC 7230 HTTP11 Message Syntax and Routing June 2014 21ClientServer Messaging HTTP is a stateless requestresponse protocol that operates by exchanging messages across a reliable transport- or session-layer connection An HTTP client is a program that establishes a connection to a server for the purpose of sending one or more HTTP requests.
The maximum size of a TCPIP packet is approximately 64 KB. The change from one state to another is called. The remainder of this document assumes SCTP runs on top of IP.
A tropical cyclone is a rapidly rotating storm system characterized by a low-pressure center a closed low-level atmospheric circulation strong winds and a spiral arrangement of thunderstorms that produce heavy rain and squallsDepending on its location and strength a tropical cyclone is referred to by different names including hurricane ˈ h ʌr ɪ k ən-k eɪ n. Peer-to-peer P2P computing or networking is a distributed application architecture that partitions tasks or workloads between peers. BitTorrent is a communication protocol for peer-to-peer file sharing P2P which enables users to distribute data and electronic files over the Internet in a decentralized manner.
Although the diagram is linear each participant may be engaged in multiple simultaneous communications. Session Initiation Protocol June 2002 enabling Internet endpoints called user agents to discover one another and to agree on a characterization of a session they would like to share. They are said to form a peer-to-peer network of nodes.
RFC 760 IENs 128 123 111 80 54 44 41 28 26 INTERNET PROTOCOL DARPA INTERNET PROGRAM PROTOCOL SPECIFICATION 1. RFC 1035 Domain Implementation and Specification November 1987 from master files stored locally or in another name server. RFC 8446 TLS August 2018 - Other cryptographic improvements were made including changing the RSA padding to use the RSA Probabilistic Signature Scheme RSASSA-PSS and the removal of compression the Digital Signature Algorithm DSA and custom Ephemeral Diffie-Hellman DHE groups.
TCP is an important transport-layer protocol in the Internet protocol stack and it has continuously evolved over decades of use and growth of the Internet. The basic service offered by SCTP is the reliable transfer of user. The size of a TCPIP packet is limited to this amount when the data is sent over an Ethernet.
This document specifies the Transmission Control Protocol TCP. Any servers you have should be connected to your router. Some networks have a server that contains centralized data and programs for all the computers connected to the network.
Physical Data Link Network Transport. The maximum size of a data packet on an Ethernet is about fifteen hundred bytes. Get 247 customer support help when you place a homework help service order with us.
ACM Transactions on Recommender Systems TORS will publish high quality papers that address various aspects of recommender systems research from algorithms to the user experience to questions of the impact and value of such systemsThe journal takes a holistic view on the field and calls for contributions from different subfields of computer science and. Automata finite automaton or simply a state machine is a mathematical model of computationIt is an abstract machine that can be in exactly one of a finite number of states at any given time. To send or receive files users use a BitTorrent client on their Internet-connected computerA BitTorrent client is a computer program that implements the BitTorrent protocol.
Over this time a number of changes have been made to TCP as it was specified in RFC 793 though these have only been documented in a piecemeal fashion. In the OSI reference model the communications between a computing system are split into seven different abstraction layers. For locating prospective session participants and for other functions SIP enables the creation of an infrastructure of network hosts called proxy servers to which user agents can.
A finite-state machine FSM or finite-state automaton FSA plural. A computer network is a set of computers sharing resources located on or provided by network nodesThe computers use common communication protocols over digital interconnections to communicate with each other. Peers make a portion of their resources such as processing power disk storage or network bandwidth directly.
The FSM can change from one state to another in response to some inputs. RFC 4960 Stream Control Transmission Protocol September 2007 12Architectural View of SCTP SCTP is viewed as a layer between the SCTP user application SCTP user for short and a connectionless packet network service such as IP. Peers are equally privileged equipotent participants in the network.
INTRODUCTION 11Motivation The Internet Protocol is designed for use in interconnected systems of packet-switched computer communication networks. These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency. Rental price 70 per night.
What Does The Permit Tcp Established Command Do Quora
Linux Based Plc For Industrial Control Linux Journal
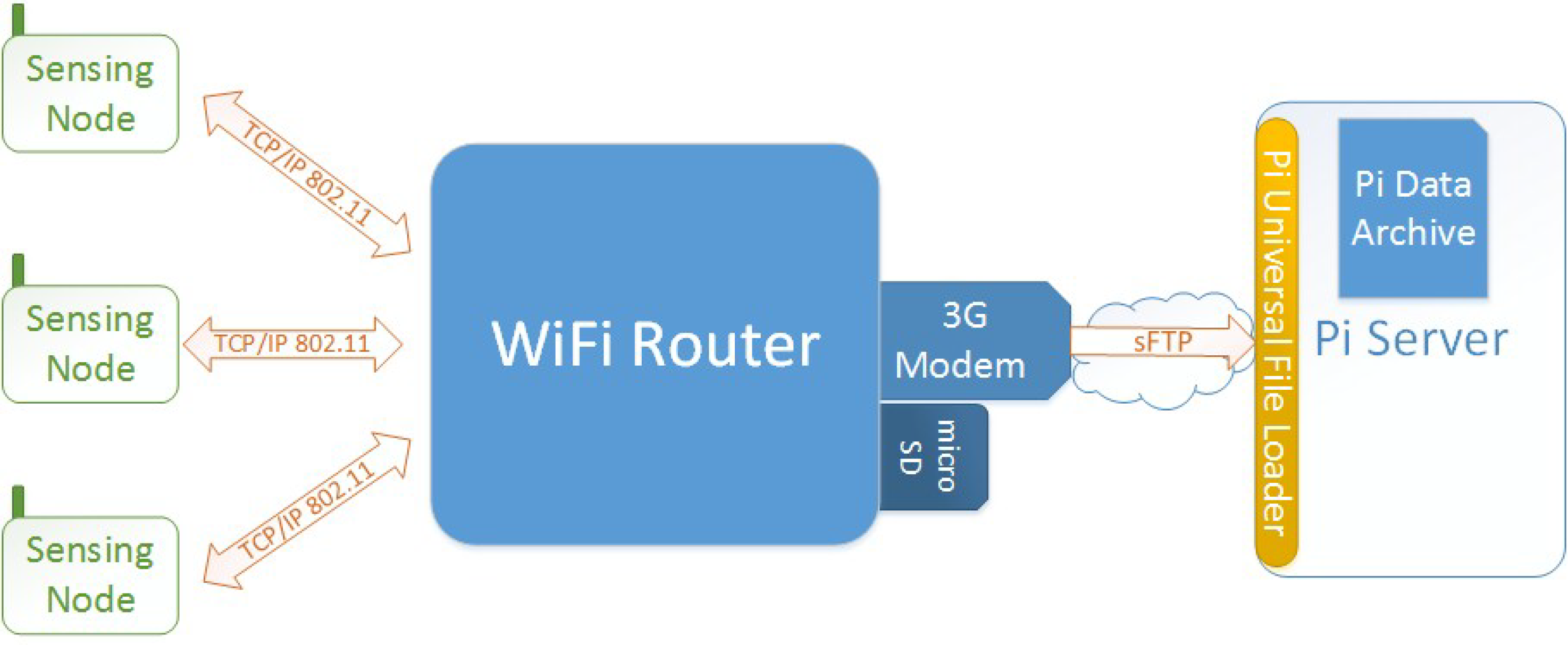
Sensors Free Full Text Building In Briefcase A Rapidly Deployable Environmental Sensor Suite For The Smart Building Html

Finite State Machine Fsm Types Properties Design And Applications
How Does Tcp Provide Reliability Quora

What Is The Function Of Tcp Timeout What Happens When Tcp Timeout Is Too Long What Happens When Tcp Timeout Is Too Fast Quora

Ebaocloud Applications Ebaocloud
2
What Is The Role Of Tcp Ip In Peer To Peer Networking Quora
How Is A Tcp Connection Terminated Quora

Netsim Experiment Manual
In A Tcp Protocol If The Reserved Space For A Source Destination Address Is 16 Bit How Can We Specify A 128 Bit Address From Ipv6 For Example Quora

Finite State Machine Fsm Types Properties Design And Applications
How Is A Tcp Connection Terminated Quora

Jenkins Noise

Finite State Machine Fsm Types Properties Design And Applications

Best Practices Noise